Setup CDR for AWS CFT¶
Overview¶
This lab will walk though setting up CloudTrail in a AWS. Then enabling the Trail as a DfAWS Data Source for CDR.
For this lab SEs should use their personal AWS account NOT the Vectra TME demo accounts!
Notes¶
In some cases an existing Trail can be used
A max of 5 Trails can be setup per AWS region
The Trail should be enabled at the org level
The first Trail is free
Anywhere you see initials your initials should be used as the value
Setting up first Trail¶
Logon to AWS Management Console (Web UI).
In the search at the top right type trails, then Click Trails.
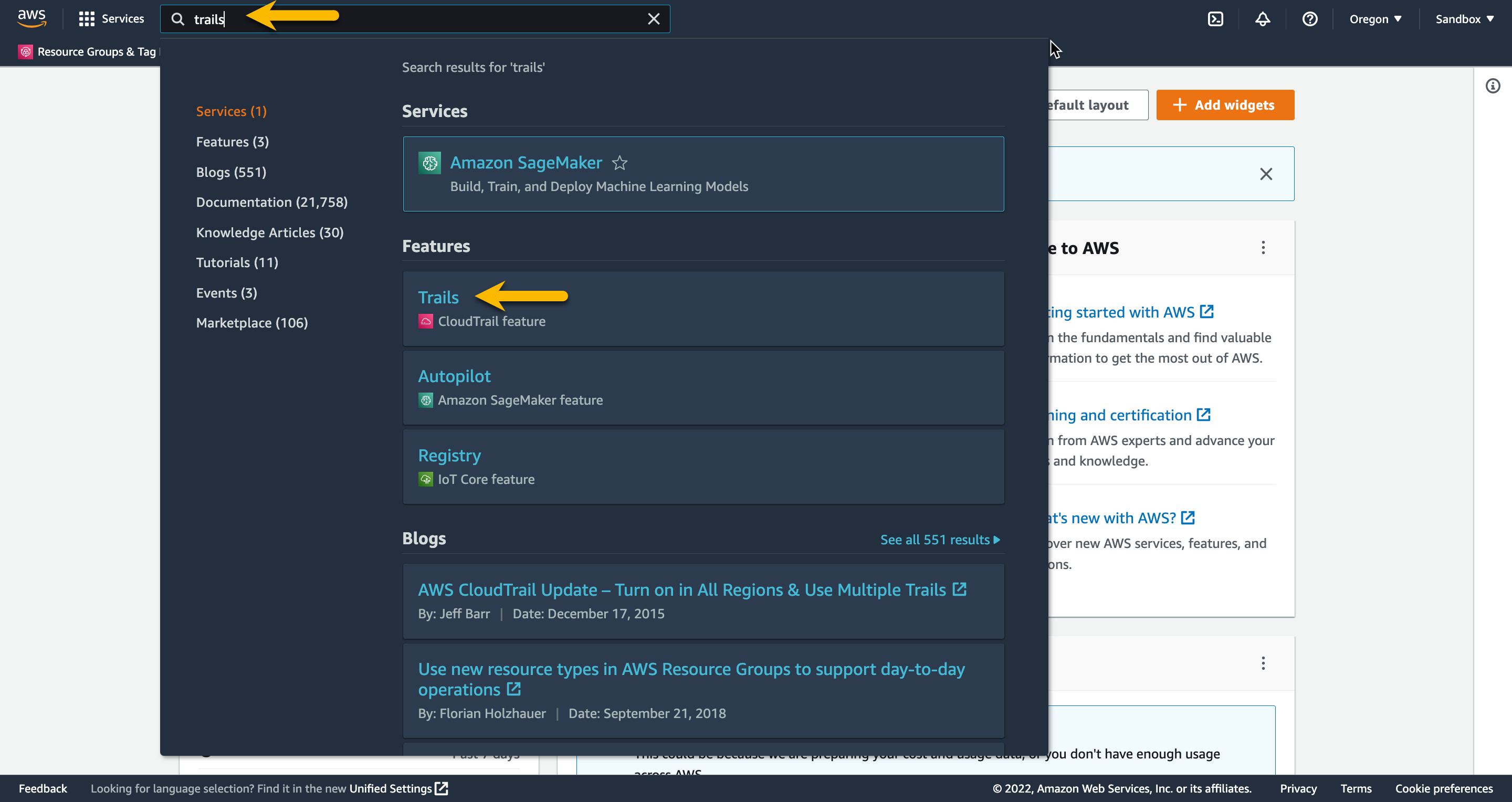
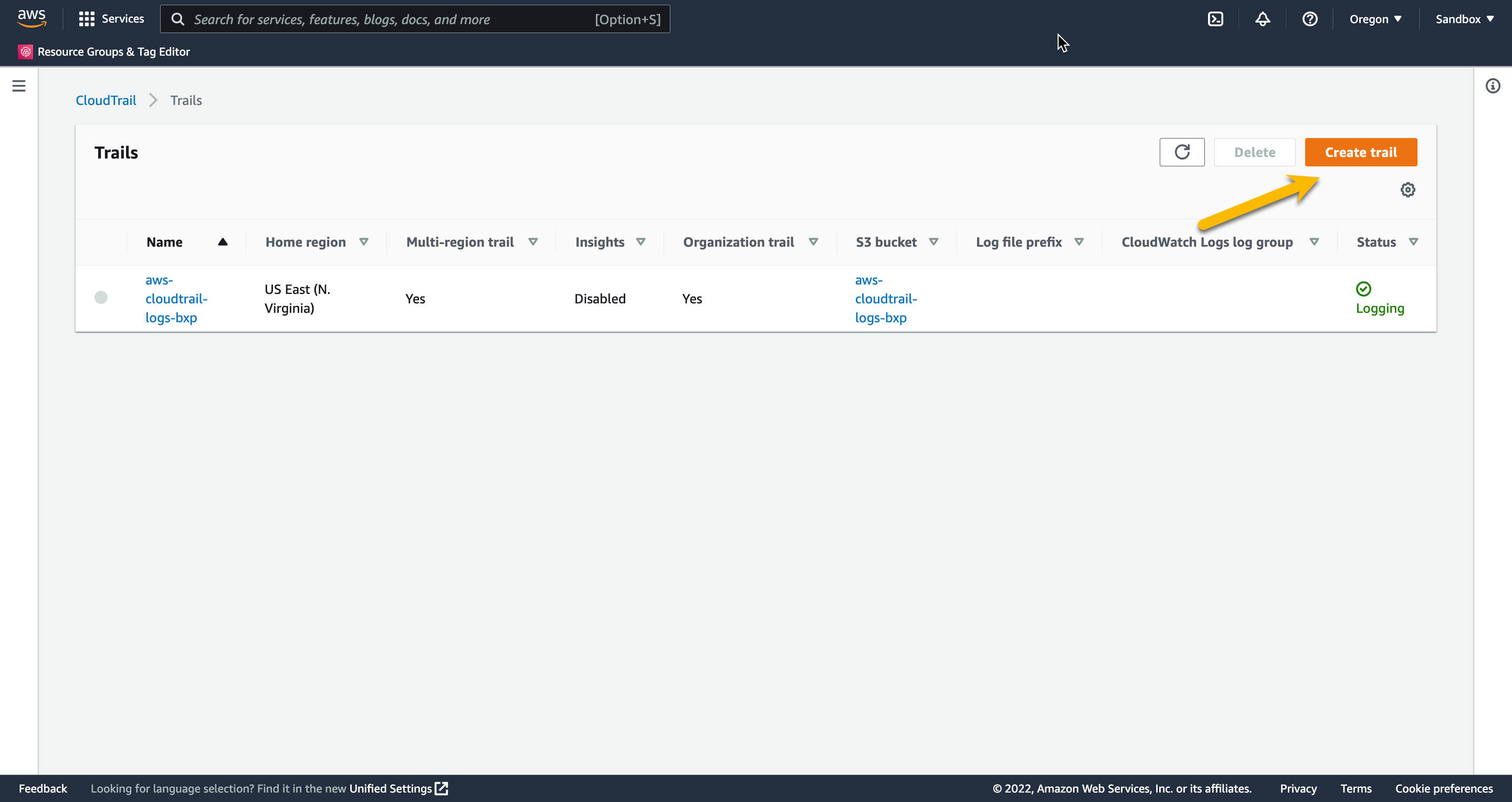
Once at the Trails page, click Create Trail on the top right.
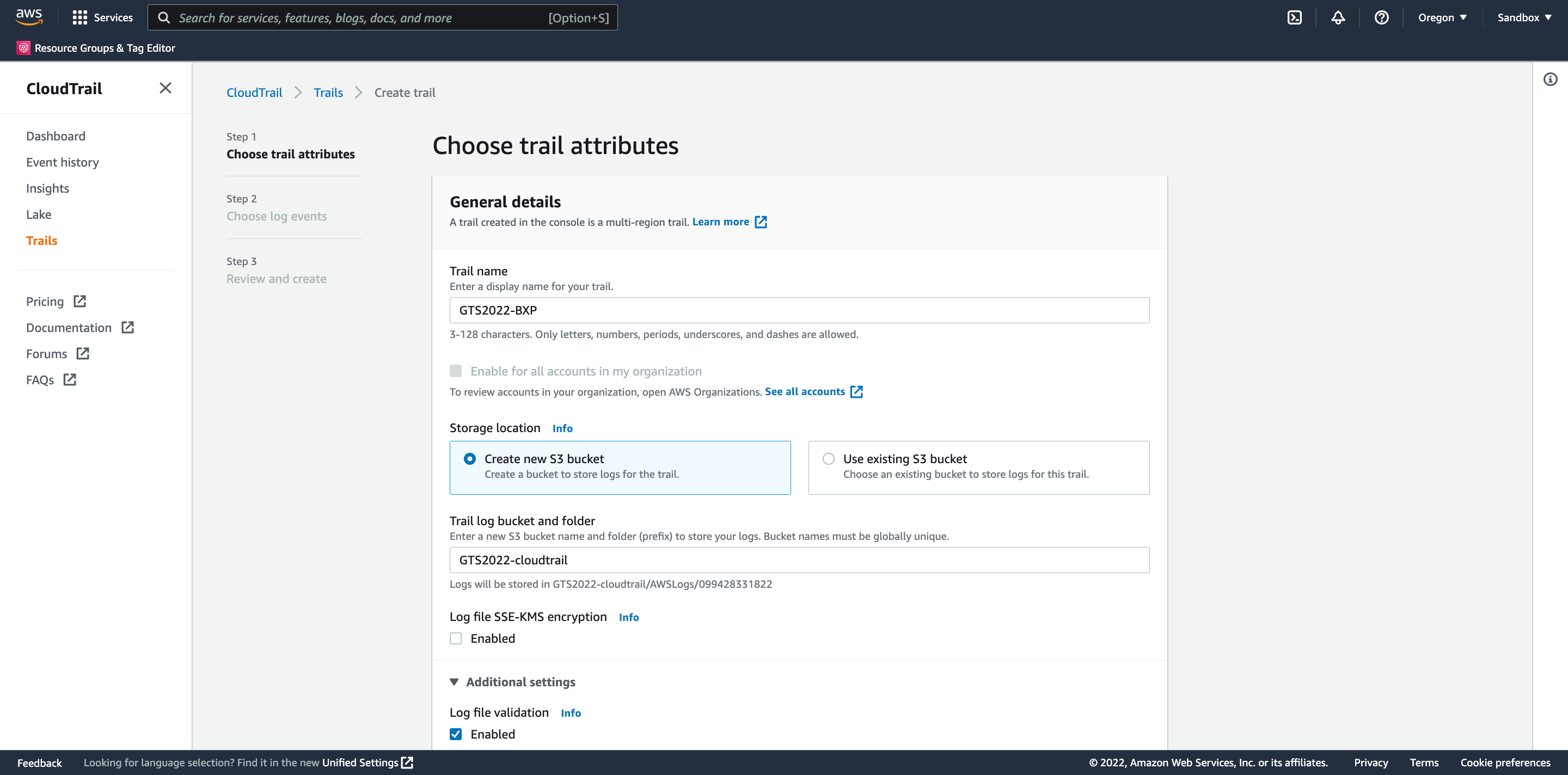
On the Create Trail Attributes page fill in the following values, and click Next:
Trail name - gts2022-initials
Storage location - Create new S3 bucket
Trail log bucket and folder - gts2022-cloudtrail-initials
Log file SSE-KMS encryption - Uncheck
All other fields should be left at defaults
On the Choose log events page fill in the following values, and click Next:
Events
Management events - Checked
Data events - Checked
Management events
Read - Checked
Write - Checked
Data events
Data event type - S3
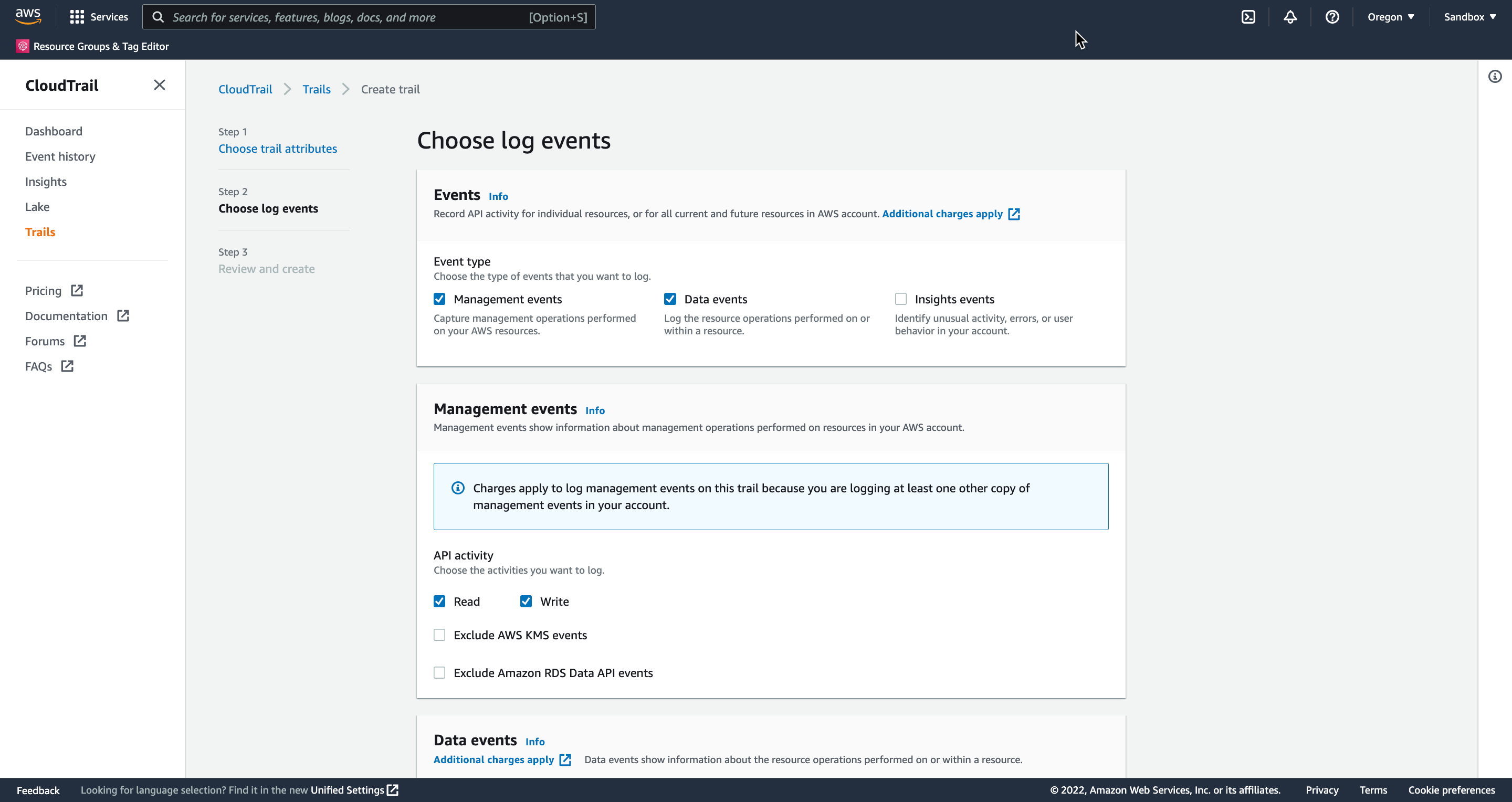
You will be taken to the Review and create page, scroll down to the bottom and click Create trail
Gather values for DfAWS Data Source¶
When you run the Cloud Formation Template (CFT) for DfAWS you will need the bucket name and region.
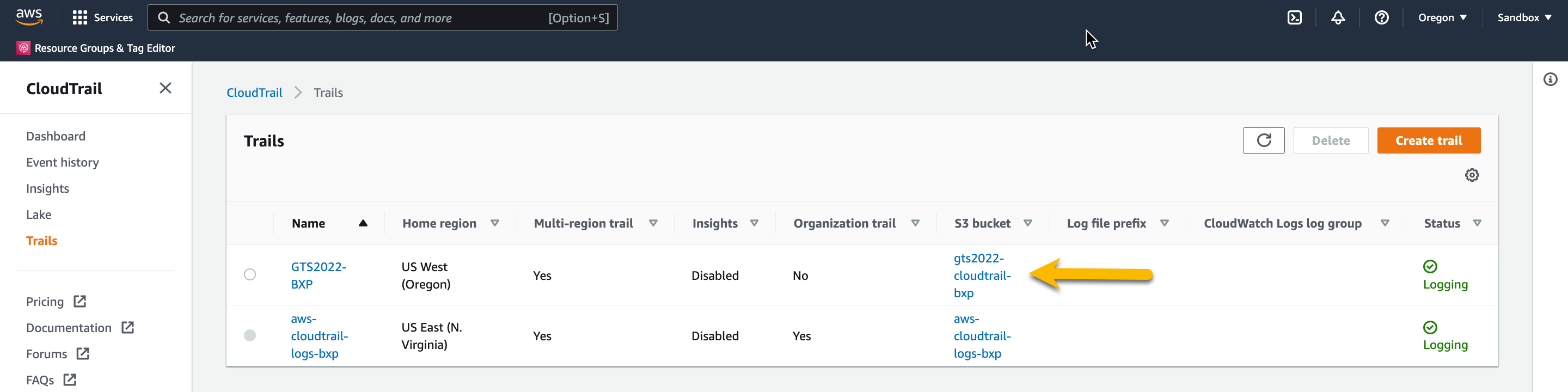
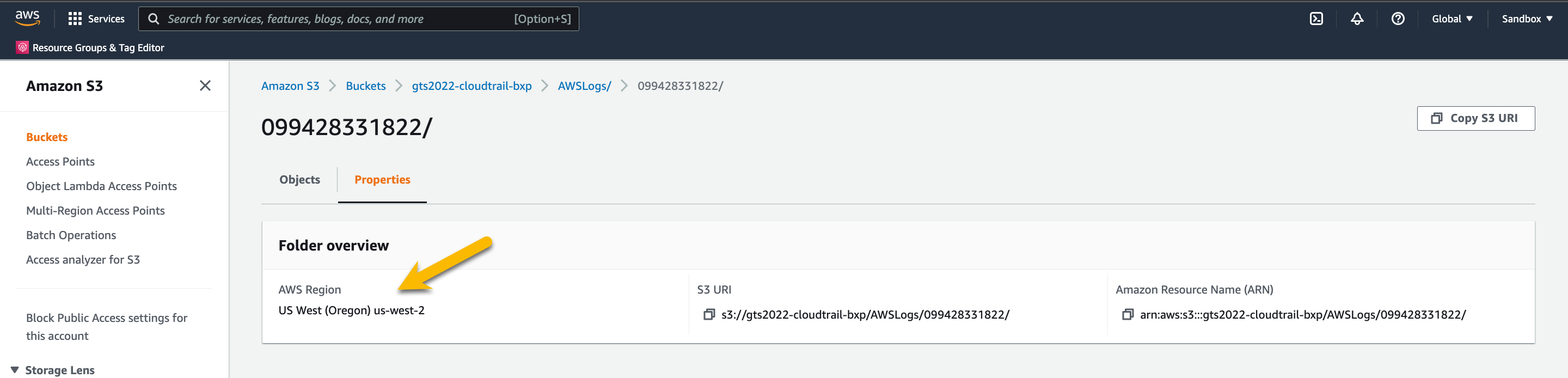
To get this, go back to your Trails page in the AWS Management Console.
Make note of the S3 bucket name, and click the S3 bucket name
Press the Properties
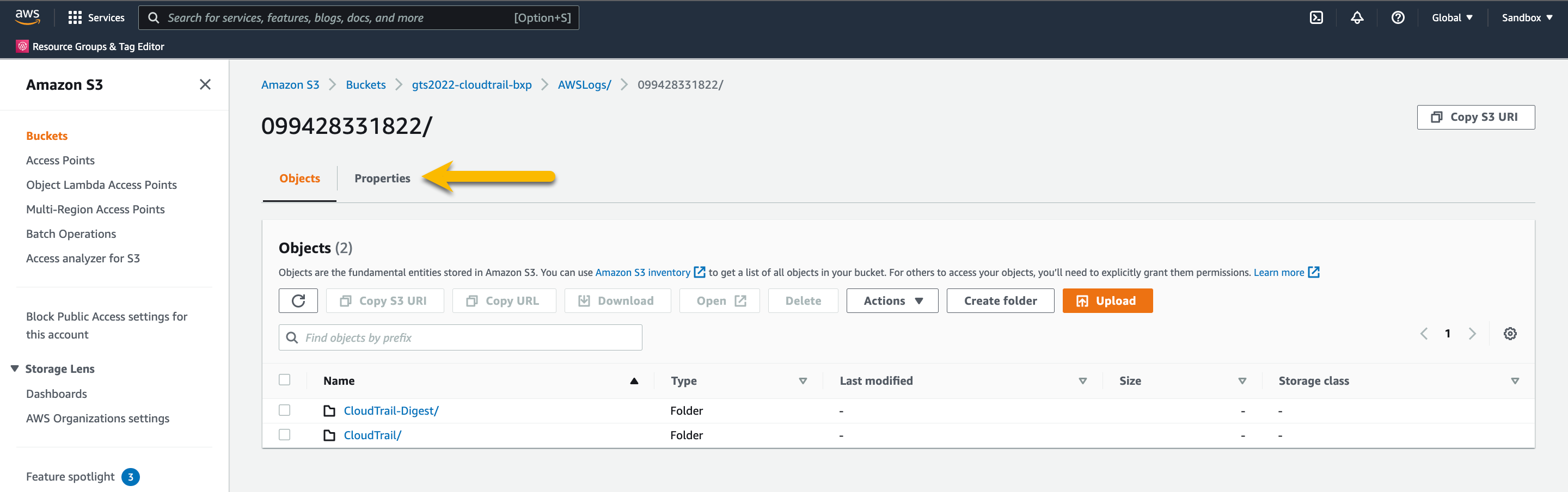
Make note of the AWS Region
Setup DfAWS Data Source¶
Logon to the DfAWS instance with SSO.
Note: Do NOT use you static username and password. The SSO accounts have been given admin privileges within DfAWS.
On the left navigation bar choose Data Sources, then on the top right click + Create AWS Connection
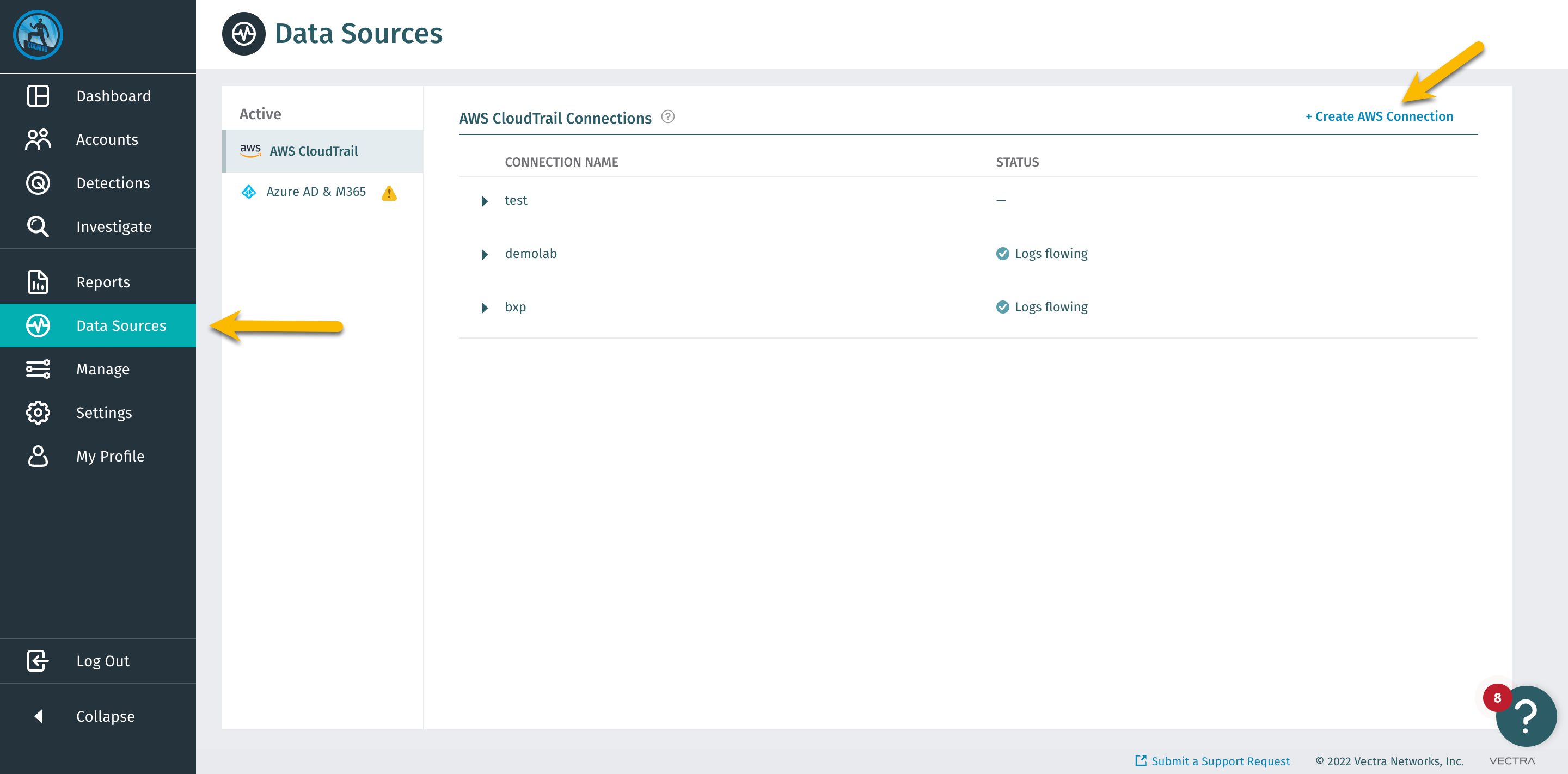
Name the connection gts2022-initials and click Create & Continue
Make sure you are still logged into your personal AWS account
Create IAM Roles
Create roles using a CloudFormation script
Region where your AWS data resides drop down - The
for you S3 bucket Click the Run this CloudFormation script to connect your S3 bucket in
This will run an AWS CloudFormation Template that creates a new role and SNS topic
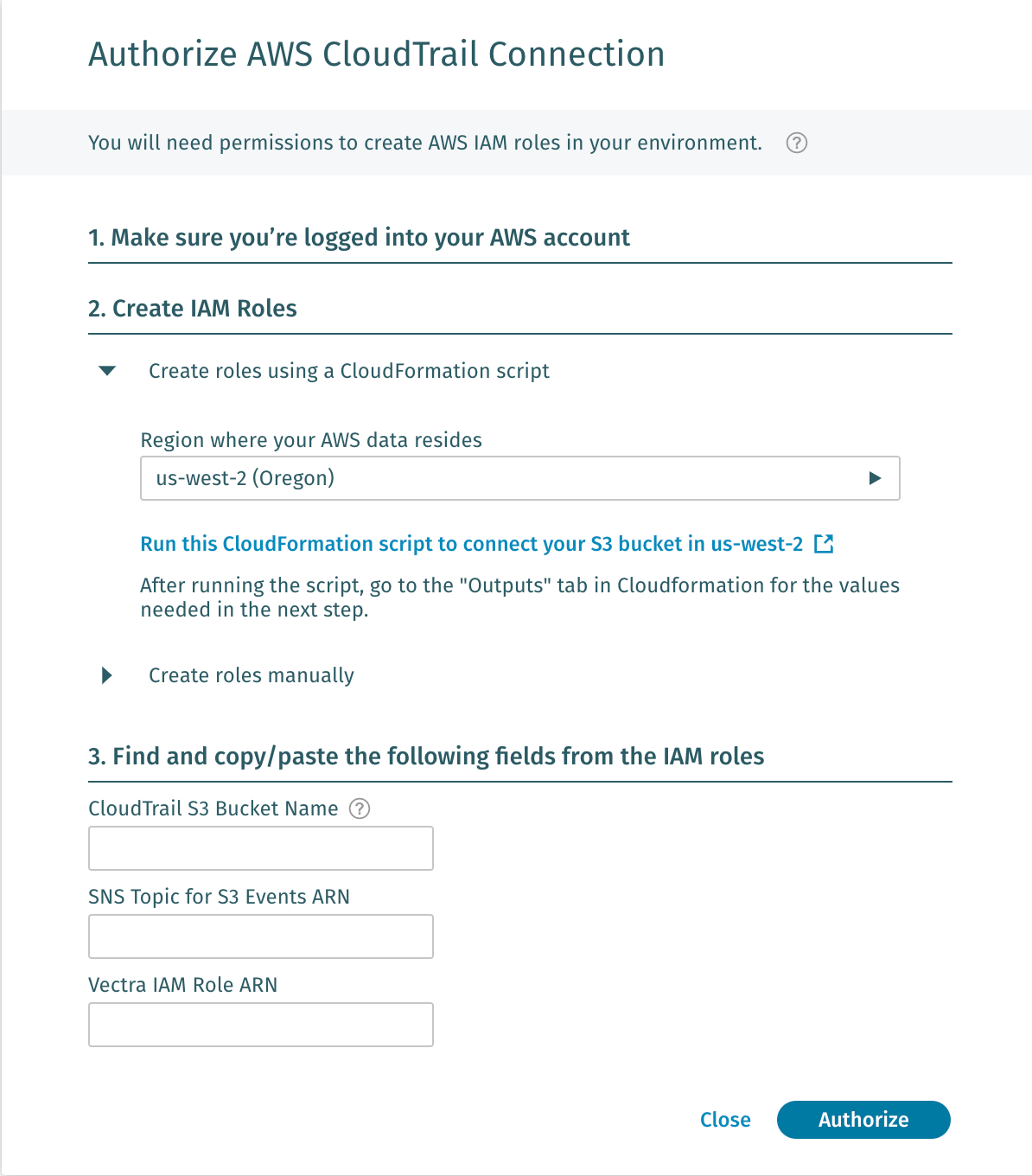
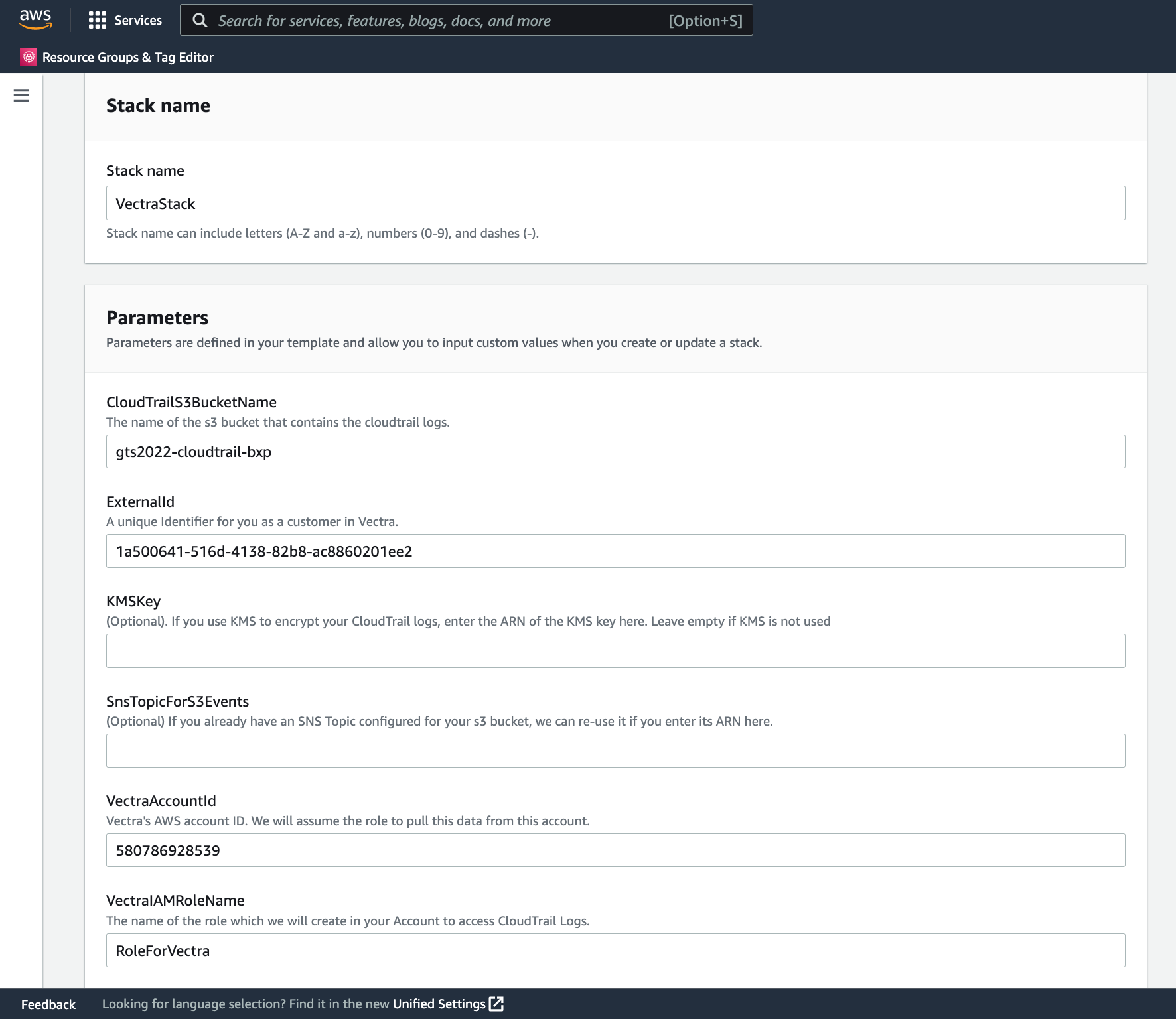
On the Stack page fill in the following values, and click Create stac:
Stack name - VectraStack (Note: Stack names can only be used once until stack is deleted*
CloudTrailS3BucketName - gts2022-cloudtrail-initials
ExternalId - do not change unique value
KMSKey - Leave blank (Note: This would only be used if we enabled Log file SSE-KMS encryption)
SnsTopicForS3Events - Leave blank (Note: This would be used if an existing bucket had an SNS topic already set)
VectraAccountId - do not change
VectraIAMRoleName - VectraIAMRoleName (Note: This is the name of the role being created)
I acknowledge that AWS CloudFormation might create IAM resources with custom names - Checked
Once the stack starts running press refresh until completed.
Click the Outputs tab
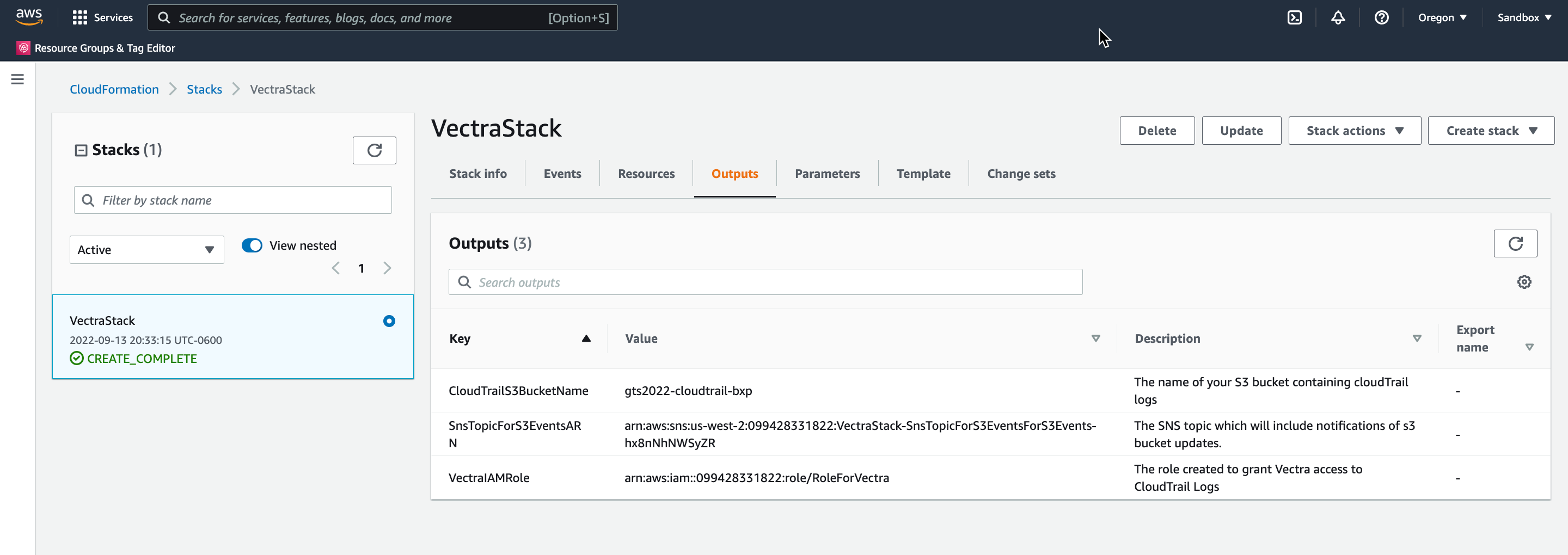
Go back to the DfAWS page and paste the fields in from the outputs page, and click Authorize.
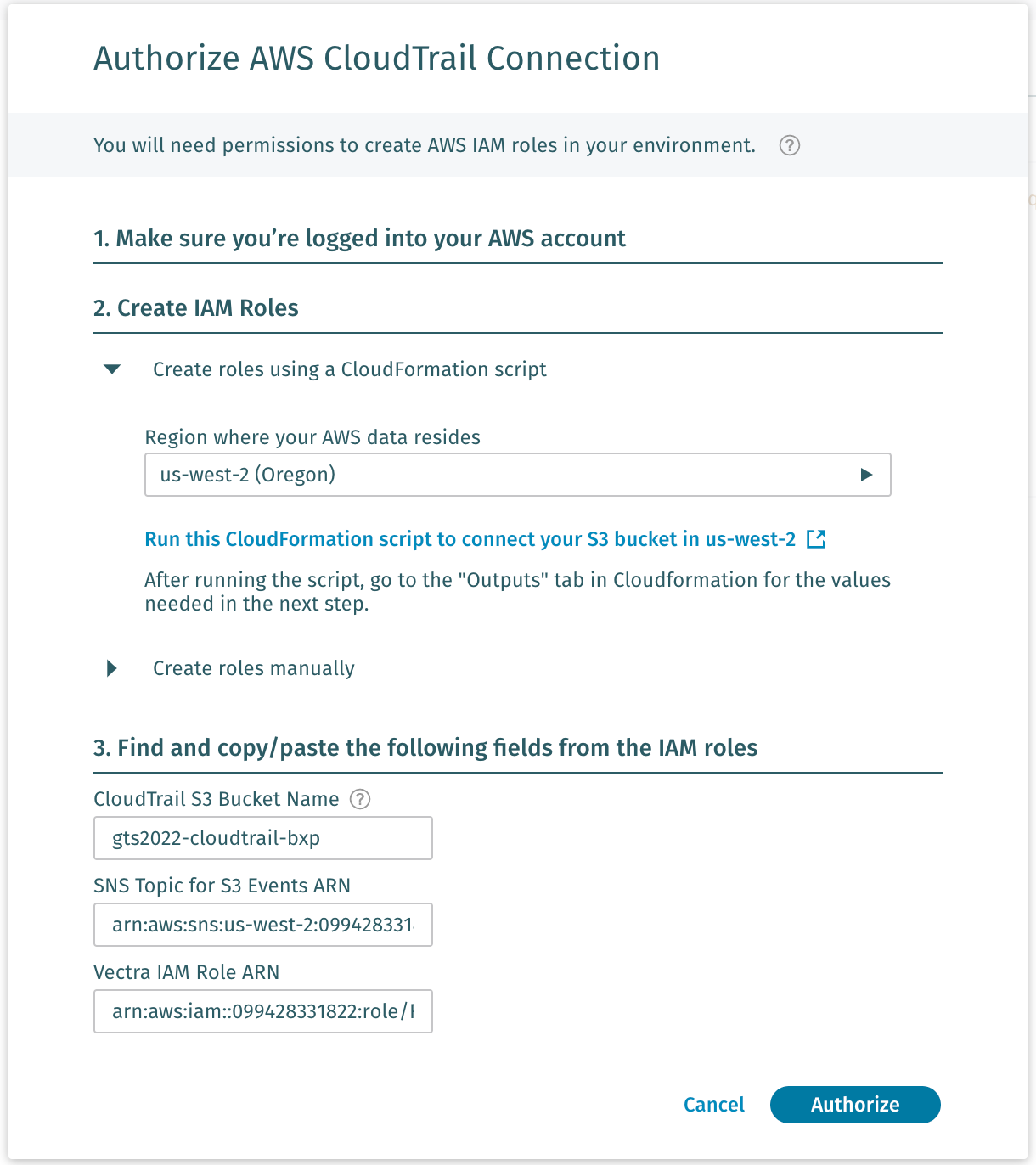
You should now see Authorization in Progress in the DfAWS console.
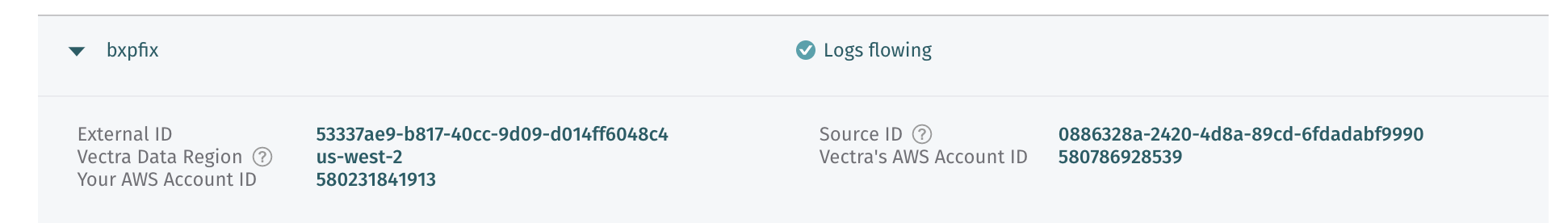
Note: This can take up to 10 minutes to complete.Once Logs flowing appears you are now ingesting CloudTrail!
Validation¶
Take a screenshot of the connection for verification